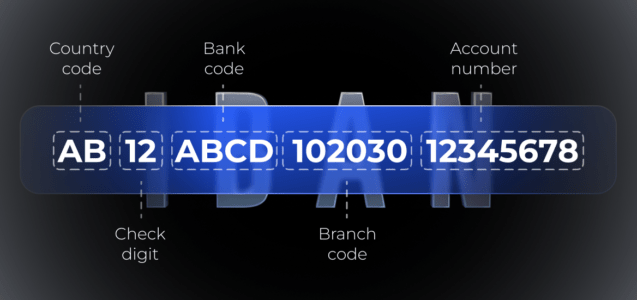
Safeguarding international payments against payment fraud is paramount to the stability and efficiency of the global economy. Ensuring these transactions are secure and trustworthy allows businesses and individuals to operate confidently across borders. It protects the parties’ financial interests by reducing the risk of fraud, identity theft, and other malicious activities.
The rise of transaction fraud has emerged as a pressing concern for businesses worldwide. The estimates indicate that for every $1 lost to fraud, a company experiences at least a $4 impact. This is particularly relevant for the iGaming industry, which has seen a staggering spike of 60% in digital fraud.
Payment fraud is a significant concern in today’s economy. It results in financial losses for businesses and consumers, damaging reputations, undermining trust, and leading to substantial legal and operational costs.
In this article, we explain to readers why online payment fraud is a big deal and why clients must find reliable payment systems with additional expertise in payment card fraud detection, protection and security.
Understanding the landscape of payment fraud in international payments
As digital transactions have become the norm, the avenues for fraud have multiplied. This landscape encompasses various deceptive activities, from traditional credit card fraud, skimming and counterfeit schemes to sophisticated cyberattacks and phishing expeditions.
As the digital realm continues to expand, vigilant and informed about the ever-evolving world of payment fraud becomes not just advisable but imperative. Let us review the most common fraud schemes affecting international payments.
Phishing attacks
Fraudsters use fake emails, phishing scams, websites, or messages designed to look like legitimate organizations or trusted contacts to deceive individuals into providing sensitive information. Often, these communications induce panic or urgency, pushing individuals to act quickly without verifying the authenticity of the request. Common tactics include warnings of account suspensions or false notifications of suspicious activity. Individuals risk exposing their bank account details or login credentials by clicking on provided links or downloading attachments.
Identity theft
Cybercriminals employ various methods, from data breaches to social engineering, to obtain personal information about an individual. Once they have sufficient details, they can impersonate that person and steal personal information, access bank accounts, take out loans, or make unauthorized transactions, often leaving the victim with debts or a tainted credit history. The repercussions of identity theft can be long-lasting and difficult to rectify.
Advance fee fraud
In these types of payment fraud, scammers promise victims significant returns on an investment or a large sum of money, usually from a lottery or inheritance. However, before they can receive this windfall, they need to pay a fee upfront, which could be disguised as taxes, legal fees, or other expenses. The money scammers promise never materialise once the fee is out there, and the scammer often disappears.
Invoice Redirection
Also known as “business email compromise,” this payment fraud involves cybercriminals intercepting or mimicking business correspondence. They convince companies that a supplier’s payment details have changed, urging them to give stolen payment information and pay outstanding invoices to a new, fraudulent account. When users reveal the deception, the funds are nowhere to be found. This leaves businesses out of pocket and potentially damaging valuable business relationships.
Man-in-the-middle attacks
In these attacks, fraudsters secretly intercept relays and possibly alter the communication between two parties who believe they are directly communicating with each other. For payment processes, this can mean that when an individual thinks they are instructing their bank to make a payment to a particular account, the fraudster redirects the person’s payment information to their own account without either party realizing it until it’s too late.
Carding
Cybercriminals use automated software to test stolen credit card information on various websites to verify its validity. Once a person confirms a fraudulent purchase, the compromised card details and data can be used for larger unauthorized transactions or sold in bulk on the dark web. This type of alternative method of credit card fraud highlights the importance of regular credit card statement checks and the use of secure and trusted payment gateways by online merchants.
Money muling
Often unknowingly, fraudsters recruit individuals to move illegally obtained money between accounts. These “mules” often think they work for a legitimate business, or scammers just deceive them into participating in fake job advertisements. The money usually happens through several accounts, often internationally, making it harder for authorities to trace the original fraudsters and their ill-gotten gains.
Understanding and recognizing the signs of these and payment fraud types is the cornerstone of safeguarding oneself and one’s business. By staying informed and implementing robust security measures, individuals and businesses can reduce their vulnerability to these potential risks.
Cost of fraud
As the international payment landscape continues to evolve, so do the tactics of fraudsters. The cost of fraud to businesses extends beyond immediate financial losses. While unauthorized transactions and deceptive practices that commit payment fraud can result in substantial monetary drains, the repercussions often ripple outwards, impacting various facets of a business.
Reputational damage, for instance, can erode customer trust, reducing loyalty and potential loss of clientele. Operational disruptions, often a fallout of online fraud, can halt business processes, leading to delays and inefficiencies. Moreover, addressing payment fraud often necessitates investments in cybersecurity enhancements, legal consultations, and public relations efforts to manage negative publicity.
There’s also the psychological toll on employees, leading to decreased morale and productivity. While the direct financial implications of payment fraud are significant, the indirect costs—ranging from brand tarnishing to internal disruptions—can be equally, if not more, debilitating for businesses.
The anatomy of secure transactions
The anatomy of secure transactions is built upon multiple layers of protection to ensure the safety and confidentiality of the data and funds involved. Here are a few crucial components:
- Authentication. Ensures that parties involved in the transaction are who they claim to be. Common methods include passwords, PINs, and biometric verifications.
- Encryption. Converts transaction details into a code, protecting sensitive data from unauthorized access. Techniques like SSL (Secure Sockets Layer) are commonly used for online transactions.
- Tokenization. Replaces sensitive data, such as credit card numbers, with unique characters (tokens) that have no meaningful value if intercepted.
- Fraud Detection. Automated systems monitor transactions for suspicious activities, alerting businesses and consumers to potential payment fraud. This often involves AI and machine learning algorithms.
- Firewalls. Act as barriers between untrusted networks and internal systems, preventing unauthorized access and fraud protection.
- Secure Payment Gateways. Trusted intermediaries that encrypt sensitive payment information and communicate with banks to ensure transaction validity.
- Regular Audits and Monitoring. Periodic checks to ensure that security protocols are up-to-date and effective against online payment fraud.
Ensuring a transaction’s security hinges on integrating these components effectively. Combined, they create a strong shield against potential threats, safeguarding both businesses and consumers.
Risk assessment: your first line of defence
Risk assessment stands as a critical foundation for safeguarding financial operations and transactions. Businesses can proactively address and mitigate threats by identifying, evaluating, and prioritizing potential vulnerabilities. Here’s a brief overview:
Risk identification
This step thoroughly analyses payment systems and processes to pinpoint potential threats and vulnerabilities. Risks can range from unauthorized or fraudulent transactions made, often due to weak or compromised credentials, to more complex system data breaches where attackers exploit vulnerabilities in software or hardware. Regularly updating and patching systems can help in the risk rules, reducing exposure to known vulnerabilities.
Quantification
After identifying risks, measuring their potential impact on the business is crucial. This involves assessing the possible financial loss, which can be direct (loss of funds) or indirect (cost of addressing the breach). Additionally, consider the operational disruption, which might include system downtimes or manual interventions, and the potential reputational damage which can lead to loss of customer trust and future business.
Assessment
This step focuses on gauging the probability or likelihood of each online payment fraud materializing. Organizations can prioritise which threats need immediate attention by understanding the frequency of past incidents and analyzing current security measures. This ensures that resources are effectively allocated to address risks that are both severe and likely to occur.
Control evaluation
Existing safeguards, protocols, and measures in place to combat threats are reviewed. This includes firewall configurations, intrusion detection systems, and manual procedures like periodic account reconciliations. Their effectiveness is evaluated against various types of payment fraud, current threats, and gaps or inefficiencies are noted for improvement.
Risk ranking
With the potential impact and likelihood of each risk understood, they can be ranked. High-impact, high-likelihood risks are typically addressed first. This ranking helps businesses allocate resources regarding money and manpower, ensuring that the most critical threats are tackled promptly.
Mitigation strategy
For each identified and ranked high-risk one, develop and implement plans to minimize or eliminate its impact. This might involve technical solutions like advanced encryption for data at rest and in transit, multi-factor authentication, or procedural measures such as training staff on security best practices, phishing identification, or creating incident response plans.
Continuous monitoring
The threat landscape is ever-evolving, with new vulnerabilities and attack vectors emerging regularly. As such, risk assessments should not be a one-time activity. Regularly review, update, and test the risk assessment process, ensuring that new threats are identified and addressed in a timely manner.
Stakeholder communication
Transparency is key in risk management. Inform all relevant stakeholders, including employees, partners, shareholders, and customers, about identified risks and the measures to counter them. This instills confidence and can also be a regulatory requirement in certain sectors or regions. Moreover, informed employees are better positioned to act as a first line of defence against threats like phishing attempts.
Multi-Factor Authentication: an extra layer of security for international payments
Nowadays, relying solely on passwords is no longer sufficient. Multi-factor authentication (MFA) elevates security measures by requiring users to provide multiple forms of identification before granting access. Here’s a snapshot of its significance in finance and international payments:
- Multiple Verification Points. MFA typically combines something the user knows (like a password), something the user has (like a smartphone or hardware token), and sometimes something the user is (like a fingerprint).
- Reduced Risk of Unauthorized Access. Even if a malicious actor obtains one form of authentication, gaining full access becomes significantly more challenging.
- Dynamic Codes. Many MFA systems use one-time codes sent via SMS or generated by an app, which expires shortly after issuance, ensuring that even intercepted codes are useless after a short period.
- Protects Sensitive Transactions. MFA can be used to verify high-value transactions or changes to account details, which is especially crucial in finance.
- User Behavior Analysis. Some advanced MFA systems can analyze user behaviour, such as typical login locations and times, adding another layer of fraud detection.
- Enhanced User Confidence. Knowing multiple security layers are in place, users often feel more confident using digital financial platforms.
- Regulatory Compliance. Many financial regulations and standards now recommend or require MFA due to its efficacy in protecting user data.
Incorporating multi-factor authentication in international payments bolsters security and underscores a commitment to safeguarding user data and assets, which is essential for trust in today’s digital financial landscape.

Monitoring and alerts: stay one step ahead in international payments
Proactive measures like continuous monitoring and timely alerts can make all the difference in deterring fraudulent transaction activities. Let us review the most significant measures.
Real-time oversight
Continuous monitoring incorporates advanced algorithms and heuristic analysis that screens every transaction as it happens. It swiftly detects anomalies, transaction fraud or behaviours by comparing them against predetermined patterns or known payment fraud indicators. Employing machine learning can improve the accuracy of real-time fraud detection, making the system smarter.
Instant notifications
Alert systems are designed to send real-time notifications to users through various means, such as SMS, push notifications, or emails. This immediate communication ensures that users are instantly informed of any unusual or potentially unauthorized activity, which is particularly useful in time-sensitive frauds like unauthorized fund transfers.
User verification
Multifactor authentication (MFA) mechanisms can be triggered for fraudulent transactions flagged as suspect. This could involve sending an OTP (One-Time Password) to a registered mobile number, requiring biometric verification, or using hardware tokens. Such measures ensure that the actual user authorizes the transaction, thus adding an extra layer of security.
Historical analysis
Sophisticated card testing fraud monitoring tools leverage big data analytics to analyze and understand past transaction patterns of users. By developing a profile of “usual” transaction behaviours, these systems can easily identify deviations from the norm, making early payment fraud detection more effective.
Tailored alerts
Modern systems allow users to customize their alert preferences. For instance, users can set thresholds, such as receiving notifications for transactions and international payments above $500 or when account details like passwords or linked email addresses change. This personalized approach enhances the user’s sense of security and control.
Enhanced compliance
For financial institutions, continuous monitoring is not just a security measure but also a compliance necessity. Regulations like the Payment Card Industry Data Security Standard (PCI DSS) or the Bank Secrecy Act require constant scrutiny of international payments, with violations potentially leading to hefty fines.
User empowerment
The power of prompt alerts extends beyond just notifications. They also empower users to take decisive actions, such as freezing their credit card accounts, initiating chargeback fraud, or swiftly changing their login credentials, thereby minimizing potential damage.
Data insights
Beyond security, continuous monitoring tools can serve as analytic instruments. They offer insights into spending patterns, transaction trends, and customer behaviours. This data is invaluable for individuals wanting to manage their finances better and for businesses looking to refine their offerings or understand customer needs.
By integrating advanced monitoring and alert systems, financial entities enhance security and foster trust, reassuring users that their assets and data are under vigilant protection.
Legal frameworks and compliance
Legal frameworks and compliance measures are pivotal in ensuring the financial ecosystem’s integrity, stability, and trustworthiness. Here’s why they matter:
| Anti-Money Laundering (AML) | Operational Integrity | Data Security |
| Legal measures actively combat the laundering of illicit funds, helping to prevent criminal activities and ensuring the legitimacy of transactions and international payments. | Regulatory compliance ensures financial institutions operate within set guidelines, preventing malpractices, improving fraud detection and ensuring a level playing field. | Laws around data protection and privacy ensure that personal and financial information remains confidential and secure. |
| Consumer Protection | International Payments | Systemic Stability |
| Legal frameworks are designed to safeguard consumers from payment fraud, misrepresentation, and other unethical practices, ensuring they are treated fairly and transparently. | International regulations harmonize financial operations across borders, facilitating global trade and investments. | Regulations are in place to prevent systemic risks, ensuring that financial crises or collapses are averted or mitigated. |
How PayDo combats international payments fraud and safeguards client funds
Ensuring security of international payments is paramount. PayDo, at the forefront of this mission, implements advanced measures to combat and prevent payment fraud and guarantee the protection of client funds.
Well-designed verification
From the outset, PayDo emphasizes user authenticity. Users embark on a de-anonymization journey for primary verification upon creating an account. Depending on the transaction amount, an automated KYC verification system comes into play, adding another verification layer to ensure genuine user engagement.
Built-in anti-fraud system
With the integration of a self-optimizing fraud management and fraud solution, PayDo offers real-time monitoring for every transaction. This vigilant watch ensures suspicious activities are swiftly detected and addressed.
PCI-DSS Level 1 Compliance
PayDo prioritizes the security of card details. When users input their card information, they are authorizing transactions on a PCI-DSS Level 1 compliant checkout—signifying that the highest industry standards are in place to guard their card details.
Extra fraud protection with 3D-Secure (3DS)
Collaboration is key. PayDo’s alliance with Tier-1 trusted bank acquirers ensures that additional layers of security checks are enforced. Whenever a user tops up their account with a card, a 3DS procedure kicks in, prompting an extra layer of authentication to safeguard the transaction.
Sophisticated encryption
PayDo understands that data integrity is vital to financial security in the digital age. Therefore, each transaction is encrypted, protecting sensitive customer data from identity theft, alterations, or breaches.
Chargeback protection
Chargebacks can be a backdoor for fraud. PayDo’s seasoned experts manage every chargeback request, meticulously vetting them to weed out unfounded claims. This meticulous approach minimizes the chances of chargeback and refund fraud, offering users peace of mind.
Through these comprehensive measures, PayDo exemplifies its commitment to offering users a secure, reliable payment terminal platform, ensuring that every transaction is smooth and safe.
PayDo’s commitment to safeguarding accounts
We recognize the importance of every client’s funds and have established measures to ensure utmost protection, regardless of the currency. PayDo doesn’t merely store your funds; we go a step further with a strong “safeguarding” process. This meticulous approach involves segregating 100% of client funds from our operational assets, ensuring they remain untouchable and secure.
In our safeguarding history, every fund is placed in a specialized segregated account designated solely for protected funds. Moreover, these funds are then deposited in a separate account held with our chosen authorized credit institution. With this dual-layered system, PayDo ensures that your money remains shielded, reinforcing our commitment to client trust and financial integrity.
Final recap
Safeguarding international payments is a cornerstone, ensuring stability and promoting efficiency across borders. As the digital era expands its horizons, payment fraud has emerged as a looming shadow, threatening the essence of our digitalized financial infrastructure. Payment fraud underscores the urgent need for individuals and businesses to gravitate towards trustworthy payment systems.
PayDo, by deploying advanced, strong measures, not only combats the menace of payment fraud but also acts as a reliable platform, guaranteeing the utmost protection of client funds. We navigate the complexities of digital finance, entrusting platforms that prioritize safeguarding becomes beneficial and essential.
Contact us to find your reliable and secure partnership! Get dedicated multicurrency IBANs for international payments and access Cross-border, SEPA, FPS and six more payment schemes.